UCPath System Access (Security)
How to Request Access to UCPath
This page explains the process for requesting UCPath access for transactors (initiators and/or approvers). Transactors are entrusted with sensitive and confidential data, so security and targeted training are critical to maintain system integrity and accuracy. Transactional UCPath access is granted only to perform assigned job duties.
- Access varies from transactor to transactor and is determined by your job duties and the organizational structure of your department and your VC area and/or Central Office.
- New or existing users need to complete training based on security roles before access is granted; supervisors need to submit the UCPath Access Form for the approvals the transactor needs to access and work within UCPath and let the transactor know what training is needed.
- Access is approved once training is completed, the UCPath Access Form is submitted and approved. Based on the Form, your HR DSA submits a KSAMS (Kuali Security Access Management System) request, and the UCI UCPath Security Administrator approves the request. You will know your access has been approved when:
- KSAMS sends a notification email that you’ve been approved for access.
- You can navigate to the UCPath pages and pull up employees you have been authorized for. Pages are shown in Roles Wiki.
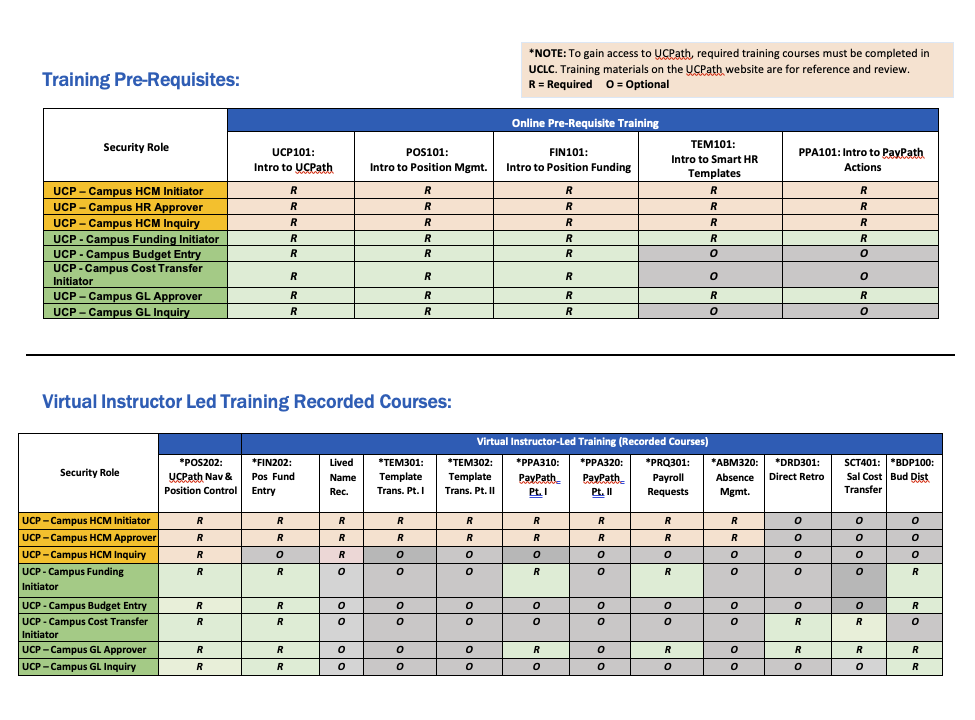
Two types of roles need to be specified for a new user to perform transactional work: Role security and Row Level security. This also determines the training that is needed in order to access UCPath. See the KSAMS Security Access Guide for UCPath Access for more details.
Roles: Controls the screens you can access and the actions you can take.
Rows: Controls whose data you can see, based on your department and business unit; this row-level security applies to all your assigned Roles.
Initiator – Transactional User
- Responsible for entering transactions into UCPath and submitting for approval.
- Primary entry role for creating and updating records.
Approver – Transactional User
- Responsible for reviewing and approving transactions.
- Reviews and approves before going to UCPath Center.
Inquiry – View-Only Access
- Has view-only access to specific UCPath pages.
Cognos Report User – Reporting Access
- Can access reports from Cognos data warehouse, not directly in UCPath.
Training is required for transactor and approver roles before having access to UCPath. This training is based on security role(s), which are determined by your supervisor based on the work you will be doing. Training requirements are listed in the Roles Wiki for each role. Training can be accessed online in the UC Learning Center (UCLC), or the Training Presentations section of the UCI UCPath website.
*R = Required
O = Optional
UCPath Access Request Process
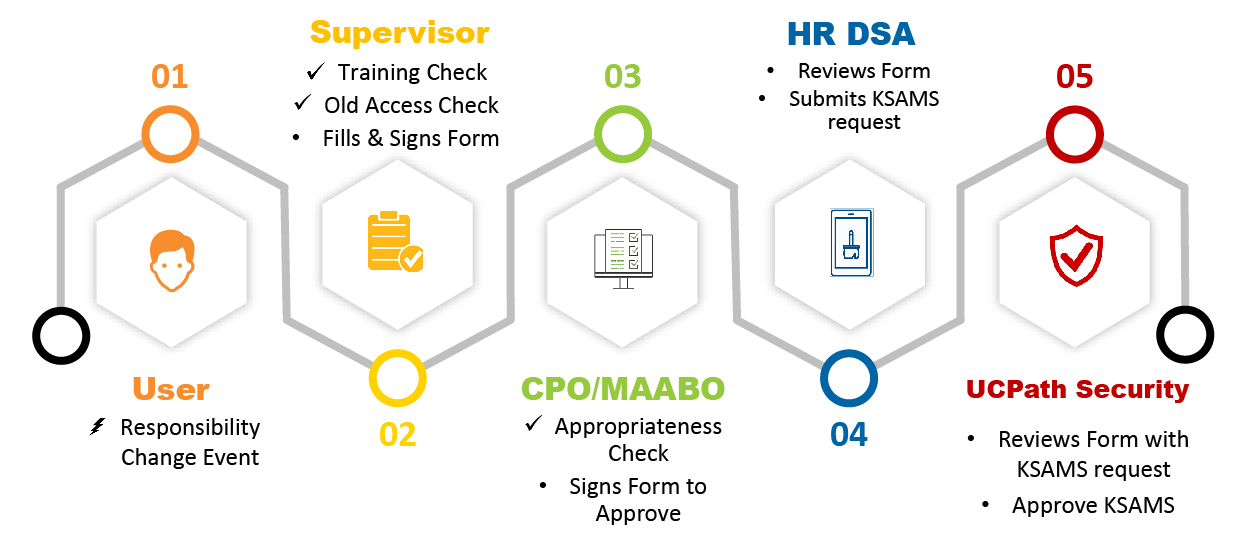
- Ask your supervisor what your security roles are and what training is required to access UCPath.
- Take required training. Training requirements are listed in the Roles Wiki for each role. Access training online in the UC Learning Center (UCLC), on the Training Presentations section of the UCI UCPath website, or via “live” Zoom training available twice a year.
- Inform your supervisor when you complete the training and ask them to complete, sign, and submit the UCPath Access Form.
- Inform new transactor of security roles and rows.
- Assign training based on these roles.
- Check old access; If the new transactor is a transfer employee (inter- or intra-campus), remove any old access since they are now in a new role.
- Complete, sign, and submit the UCPath Access Form once the transactor has completed training. This form requires three signatures: yours (supervisor) and a CPO, MAABO, or HR Business Partner. The Security team (HR DSA) will then review the form and consider the approval request.
- Review the completed UCPath Access Form.
- If the form is completed properly and you agree that access is appropriate for the transactor, sign the form to approve it.
- Review the form.
- Submit a KSAMS request for access for the transactor if you agree that access is appropriate and the form has the required signatures.
- Review the form and the KSAMS request.
- Approve KSAMS.
Once training is completed and the UCPath Access Form is approved, you will be able to access UCPath.
You will know your access has been approved when:
- KSAMS sends a notification email that you’ve been approved for access
- You can navigate to pages shown in Roles Wiki
- You can bring up the people online whom you are approved to process
Please direct questions regarding your eligibility for access to your supervisor, department head,
or open an EEC ticket at UCPath Transaction Security Inquiry web page.
Training
Training requirements are listed in the Roles Wiki for each role. Access training online in the UC Learning Center (UCLC) or on the Training Presentations section of the UCI UCPath website.
Questions
UCPath Roles by Functional Area
Roles Wiki
Your primary resources to help understand what security roles you need are on this UCPath system access web page, and the UCPath Roles Wiki below.
Roles for users who perform Human Resources transactions or approve them. These transactions include hire, extended absences, PayPath, Forms, position management, and time upload.
Users who have accounting or budgeting responsibility to maintain position funding, Work Study inquiry, funding entries, direct retros, or benefits cost transfers.
The Benefits module in UCPath is automated in enrolling employees into benefits programs based on rules and criteria. With the role of Health Care Facilitator, a user can maintain information on beneficiary and their dependents.
Roles for users who perform support functions, such as supporting approvals process (AWE), view security information, view error reports for failed processes.